

St.executeUpdate(sql); sql = "INSERT INTO SchMIS " + "VALUES (004, 'Nihal J.K', '12C')";

| Command | Example | Description | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| cat | Sends file contents to standard output. This is a way to list the contents of short files to the screen. It works well with piping. | |||||||||||||||||
| cat .bashrc | Sends the contents of the ".bashrc" file to the screen. | |||||||||||||||||
| cd | Change directory | |||||||||||||||||
| cd /home | Change the current working directory to /home. The '/' indicates relative to root, and no matter what directory you are in when you execute this command, the directory will be changed to "/home". | |||||||||||||||||
| cd httpd | Change the current working directory to httpd, relative to the current location which is "/home". The full path of the new working directory is "/home/httpd". | |||||||||||||||||
| cd .. | Move to the parent directory of the current directory. This command will make the current working directory "/home. | |||||||||||||||||
| cd ~ | Move to the user's home directory which is "/home/username". The '~' indicates the users home directory. | |||||||||||||||||
| cp | Copy files | |||||||||||||||||
| cp myfile yourfile | Copy the files "myfile" to the file "yourfile" in the current working directory. This command will create the file "yourfile" if it doesn't exist. It will normally overwrite it without warning if it exists. | |||||||||||||||||
| cp -i myfile yourfile | With the "-i" option, if the file "yourfile" exists, you will be prompted before it is overwritten. | |||||||||||||||||
| cp -i /data/myfile . | Copy the file "/data/myfile" to the current working directory and name it "myfile". Prompt before overwriting the file. | |||||||||||||||||
| cp -dpr srcdir destdir | Copy all files from the directory "srcdir" to the directory "destdir" preserving links (-p option), file attributes (-p option), and copy recursively (-r option). With these options, a directory and all it contents can be copied to another directory. | |||||||||||||||||
| dd | dd if=/dev/hdb1 of=/backup/ | Disk duplicate. The man page says this command is to "Convert and copy a file", but although used by more advanced users, it can be a very handy command. The "if" means input file, "of" means output file. | ||||||||||||||||
| df | Show the amount of disk space used on each mounted filesystem. | |||||||||||||||||
| less | less textfile | Similar to the more command, but the user can page up and down through the file. The example displays the contents of textfile. | ||||||||||||||||
| ln | Creates a symbolic link to a file. | |||||||||||||||||
| ln -s test symlink | Creates a symbolic link named symlink that points to the file test Typing "ls -i test symlink" will show the two files are different with different inodes. Typing "ls -l test symlink" will show that symlink points to the file test. | |||||||||||||||||
| locate | A fast database driven file locator. | |||||||||||||||||
| slocate -u | This command builds the slocate database. It will take several minutes to complete this command. This command must be used before searching for files, however cron runs this command periodically on most systems. | |||||||||||||||||
| locate whereis | Lists all files whose names contain the string "whereis". | |||||||||||||||||
| logout | Logs the current user off the system. | |||||||||||||||||
| ls | List files | |||||||||||||||||
| ls | List files in the current working directory except those starting with . and only show the file name. | |||||||||||||||||
| ls -al | List all files in the current working directory in long listing format showing permissions, ownership, size, and time and date stamp | |||||||||||||||||
| more | Allows file contents or piped output to be sent to the screen one page at a time. | |||||||||||||||||
| more /etc/profile | Lists the contents of the "/etc/profile" file to the screen one page at a time. | |||||||||||||||||
| ls -al |more | Performs a directory listing of all files and pipes the output of the listing through more. If the directory listing is longer than a page, it will be listed one page at a time. | |||||||||||||||||
| mv | Move or rename files | |||||||||||||||||
| mv -i myfile yourfile | Move the file from "myfile" to "yourfile". This effectively changes the name of "myfile" to "yourfile". | |||||||||||||||||
| mv -i /data/myfile . | Move the file from "myfile" from the directory "/data" to the current working directory. | |||||||||||||||||
| pwd | Show the name of the current working directory | |||||||||||||||||
| more /etc/profile | Lists the contents of the "/etc/profile" file to the screen one page at a time. | |||||||||||||||||
| shutdown | Shuts the system down. | |||||||||||||||||
| shutdown -h now | Shuts the system down to halt immediately. | |||||||||||||||||
| shutdown -r now | Shuts the system down immediately and the system reboots. | |||||||||||||||||
| whereis | Show where the binary, source and manual page files are for a command | |||||||||||||||||
| whereis ls | Locates binaries and manual pages for the ls command.
# 1: cd
The "Change Directory" command enables you to navigate to another directory. The cd command is THE most important command there is in linux i think. As the command suggests, it enables the user to change / jump to a directory. Example: cd Downloads Example: cd /etc/ Example: cd .. (Directory up!) note: Afther you have typed cd and entering the first or two letters of the directory you can press the TAB key to autocomplete the directory! so... cd Do (press tabkey) will autocomplete it to Downloads. i use this a lot <-- #2: man The man command shows the users the "manual" of the command. In some situation you might need to get more information about the command you are using. The man command shows you this information about the command. Example: man cp This will open up the "cp" manual document for us in the shell. The manual shows us the parameters available for the commands. note: To close the manual simply press "Q". #3: ls In the absolute top 15 there's no way the ls command is missing. On the third place, the ls command. The ls command is used to list the files/directories within a directory. Example: ls It shows us the directories available. #4: cp The cp command is available for us to "Copy" things. This might be usefull for duplicating files f.e. Example: cp file file2 note: file is on this case the file the user wants to be copied... file2 is the name of the copied file. It's that simple. #5 mv The mv command is used for "Move" operations. The mv commands enables the users to move a file/directory to a specified location. Example: mv /home/bas/Desktop/bla /home/bas/Desktop/fiets note: the first part of the command is the file that has to be moved. The second part (after the whitespace) is the target directory. Make sure you type in the full path using this command! #6 mkdir This command is used to "make" directories, NOT Files.. (thit is possible with another command which i will bring up later in this tutorial) Example: mkdir testdirectory note: The name of the directory is case sensitive which means that Testdirectory is a complete different directory as testdirectory. #7 rmdir When you are able to make directories, you also want to know how to remove them. Removing directories is done by the rmdir command and belongs to the absolute basic commands in shell bashing. Example: rmdir fiets note: When the directory is not empty the command will prompt an error message: rmdir: failed to remove `fiets': Directory not empty So make sure it's completely empty before removing it. #8 touch Now we know how to make directories and deleting them, i now want to use the touch command. The touch command is used to make files. Example: touch vogel This will create the file vogel for us in the directory. #9 rm The rm command stand for remove. The rm command is used in order the delete files instead of directories. Example: rm vogel note: To remove files you must have the right permission bits set on the specific file. #10 tar Sometimes you have to archive files. Archiving files is a way to pack a set of files to one single file. The operation is done by the tar command. Example: tar -cvf test.tar test (Creating a tar file from directory or file test) Example: tar -xvf test.tar myexctractfolder (Extracts the particular tar file in the current working directory) In the example i used parameters. These parameters are telling the tar command how to behave and how to execute. After the parameters i entered the name of the file which is test.tar. The second part is the source directory/file of the tar file. In this situation a directory called test. #11 pwd Sometimes you really wonder where you are in the system. PWD is the solution for that problem. PWD stands for Path Working Directory. Example: pwd #12 ifconfig ifconfig is a command showing you information about the ethernet adapters on your system. It contains very usefull information like gateway, ip, and packet statistics. For the average user this command is rarely used, but i think it's worth knowing it. Example: ifconfig note: To gain information about the wireless adapters on your system type iwconfig. #13 locate Locate is an extremely fast seaching command. It shows the directories or files each on a new line. Example: locate syslog Example: locate syslog | more (Piping structure used to invert the data from locate to the more command) note: Some keywords returns enormous ammounts of hits. Use MORE to (see example) clear things up a bit. #14 ping Ping is used as a network diagnostic command by professionals. Ping offers information about the network we are on and if the other system responds to us. In cases of troubleshooting network related problems, ping can do a great job to determine the domain of the problem. Example: ping www.google.com The command returns the interval and % of loss during the test. note: You can stop ping bij pressing crtl-c at the same time. #15 chmod The chmod command. The chmod command comes from "Change Mode" back to the unix times. It's a great command to restrict access to directories or files. But before i show you an example on how to use it, some theory. Chmod is qiet an advanced command to use. So therefore you really need to understand how it works. chmod works with so called persmission bits. These bits can be set to a certain level of restrictions. We have the following bits available:
source: http://en.wikipedia.org/wiki/Chmod
|
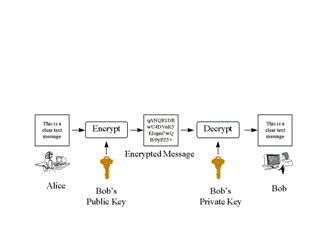


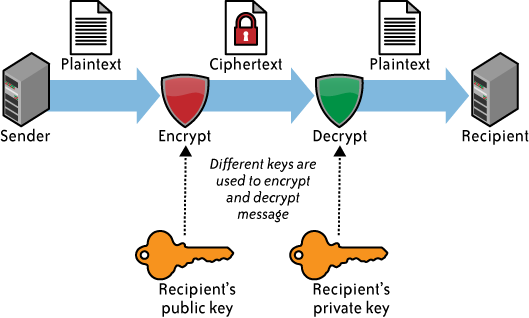
C = E(M)', and decryption with 'M = D(C)'. In order for encryption and decryption to do anything useful, the equality M = D(E(M)) will automatically hold (otherwise we do not have a way of getting plain text back out of our cipher text).C = E{k}(M)' and 'M = D{k}(C)' denote these. For keyed functions, our corresponding automatic equality is M = D{k}(E{k}(M)). With different key indexes to our function classes, we do not expect equalities like the above (in fact, finding them would usually indicate bad algorithms): M != D{k1}(E{k2}(M)). This inequality works out nicely because all the folks without access to the key K will not know which decryption function to use in deciphering C.
A Sector in the context of computing refers to a small area of a storage device, for example a hard disk drive.
For instance, a typical hard disk drive when low-level formatted is split into tracks, sectors and clusters :

In the example above in fig 1.1 we have only illustrated one track, one sector and one cluster, but you can see where the other tracks, sectors and clusters would reside.
A typical hard drive may have 30 or more tracks and 10 or more sectors per track. The size of a cluster will vary depending on the size of the partition.
Bad Sector
A bad sector refers to a single sector that has some physical flaw, although a disk can operate with a bad sector, any data that was stored in that sector will be lost, further, no data can be written to that sector.
Lost Cluster
A lost cluster is a cluster that the operating system has classed as being in use, but actually contains no data. The ScanDisk utility within Windows is designed to search for lost clusters and make them available to the file system again.
The Boot Process and the boot sector
Before the boot sector is read, the computer's bios will call a small program called an MBR (Master Boot Record) which normally resides in the first record of the first disk. The MBR will query the FAT (File Allocation Table) to establish the primary partition and then pass control over to the boot sector of that partition. The small program stored in the boot sector is then executed and the operating system will begin to load. | |